User credentials are necessary as part of a robust security access control system to demonstrate a person’s authorization to enter. The use of cards, pin codes, fingerprints, facial recognition, etc. was combined with multi-system support. Ensure that the premises are protected to the highest level of security standards.
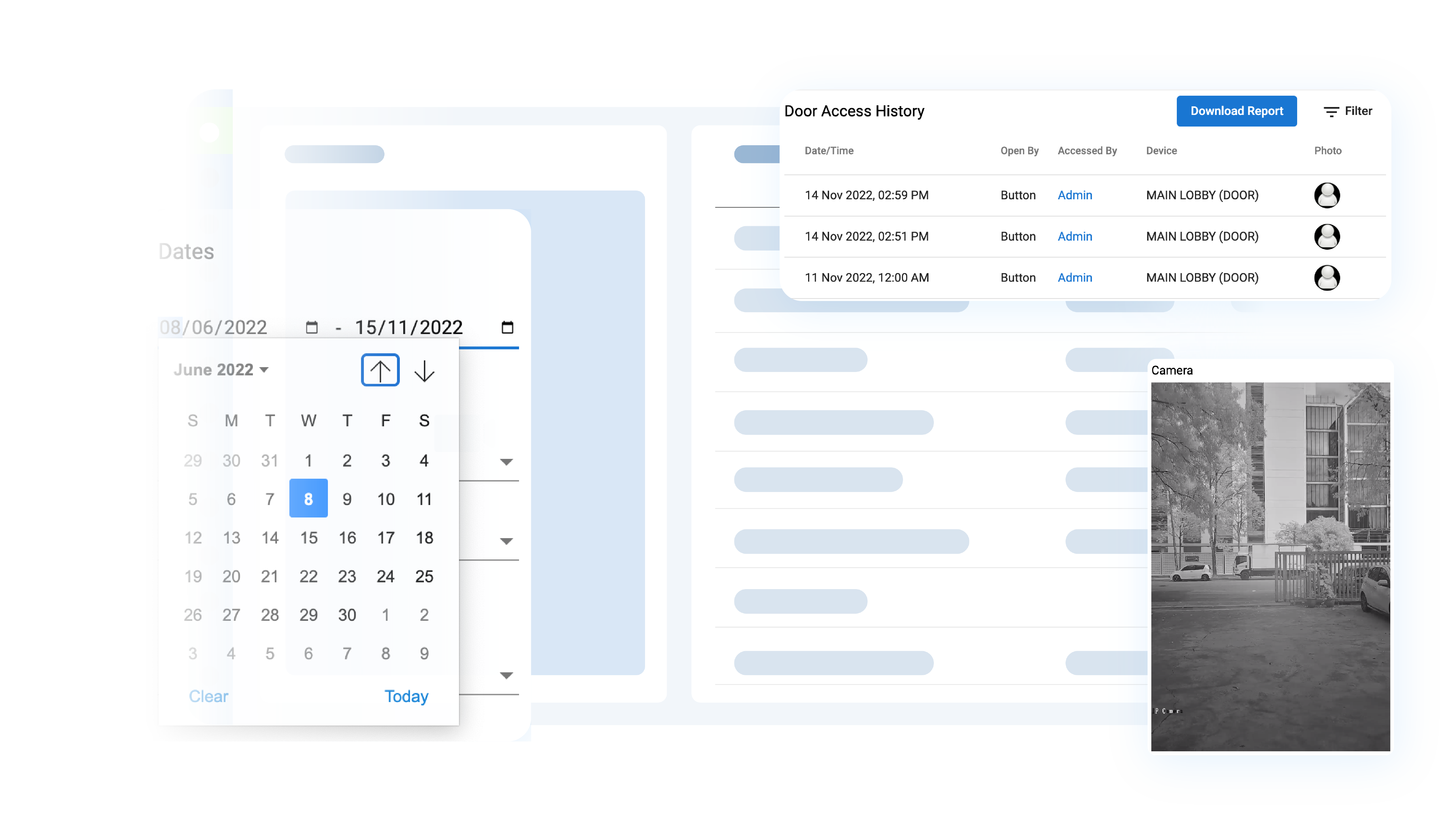
As part of the innovative approach to problem-solving that we bring to every project, we provide the ability to control and monitor any number of doors that are integrated with IP Camera Systems, with simple video integration.
User credentials are necessary as part of a robust security control system to demonstrate a person’s authorization to enter. The use of cards, pin codes, fingerprints, facial recognition, etc. was combined with multi-system support. Ensure that the premises are protected to the highest level of security standards.

As part of the innovative approach to problem-solving that we bring to every project, we provide the ability to control and monitor any number of doors that are integrated with IP Camera Systems, with simple video integration.
Integrated lock and release the door control or validate user access
Video integration at locations to view where door access is requested
Utilize 2-step verification on the admin system for higher levels of security.

